
Celebrity Nude Photos Leaked Due to Massive iCloud Backdoor – Is iOS Still the “Safest OS”?
4 min read
The Fappening will go down as one of the craziest days in tech history.
On Sunday, August 31, 2014, a hacker released nude photos of dozens of celebrities on 4Chan and Reddit.
The identity of the hacker is unknown but a lot of people are really mad. That hacker somehow managed to find his/her way into the private iCloud files of numerous celebrities.
 Apple, so far, has remained totally quiet about the leak. People are demanding an explanation.
A truthful response from Apple may look something like this:
“We install secret backdoors on all our devices and operating systems. In this instance, our iCloud backdoor was discovered and infiltrated. We’re not very good at security stuff.”
That’s a truthful response you’ll never get from Apple. Android fans love rubbing Apple’s face into their mistakes. But is Apple really to blame for this leak? Maybe not.
Apple, so far, has remained totally quiet about the leak. People are demanding an explanation.
A truthful response from Apple may look something like this:
“We install secret backdoors on all our devices and operating systems. In this instance, our iCloud backdoor was discovered and infiltrated. We’re not very good at security stuff.”
That’s a truthful response you’ll never get from Apple. Android fans love rubbing Apple’s face into their mistakes. But is Apple really to blame for this leak? Maybe not.
 That may have happened here with iCloud. All of the photos appeared to have been stolen from iCloud and metadata from the photos reveals they were taken with iPhones.
If the hacker did gain access to a backdoor, he would theoretically have free access to go around to the iCloud accounts of various celebrities and download all the nude pictures he could find.
That may have happened here with iCloud. All of the photos appeared to have been stolen from iCloud and metadata from the photos reveals they were taken with iPhones.
If the hacker did gain access to a backdoor, he would theoretically have free access to go around to the iCloud accounts of various celebrities and download all the nude pictures he could find.
 After clicking the “Forgot my password” link the perpetrator would still have to guess a security question. Unfortunately for celebrities, it’s difficult to setup a secure security question. You can easily find out Jennifer Lawrence’s mom’s maiden name, for example, or read a gossip article talking about where she lived as a kid or what kind of dog she had growing up.
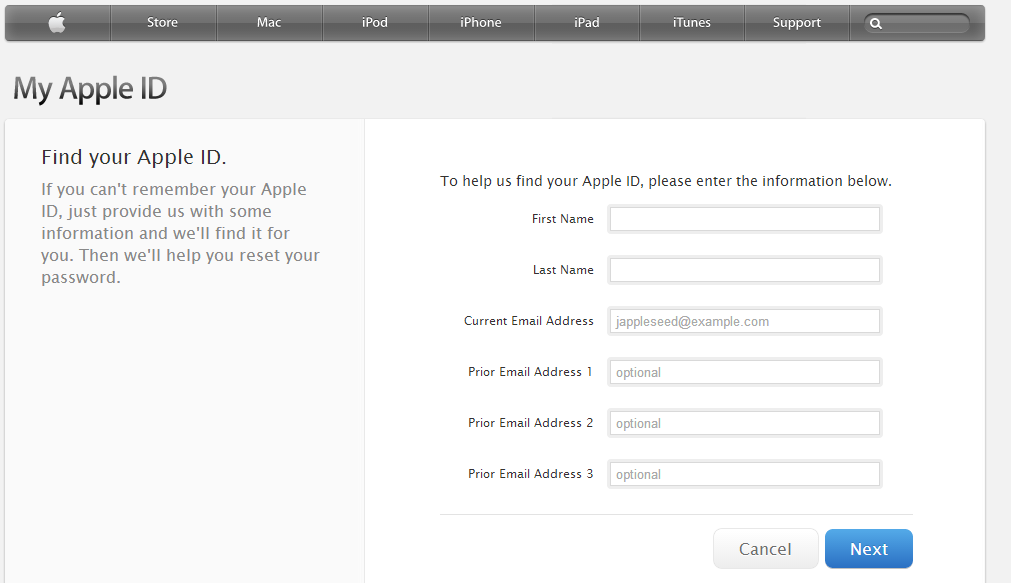
iCloud also has a feature where you don’t need to know the Apple ID at all – you can actually find the Apple ID simply by typing your name, email address, and prior email addresses into a form.
Could this feature have been used to gain access to celebrity accounts?
After clicking the “Forgot my password” link the perpetrator would still have to guess a security question. Unfortunately for celebrities, it’s difficult to setup a secure security question. You can easily find out Jennifer Lawrence’s mom’s maiden name, for example, or read a gossip article talking about where she lived as a kid or what kind of dog she had growing up.
iCloud also has a feature where you don’t need to know the Apple ID at all – you can actually find the Apple ID simply by typing your name, email address, and prior email addresses into a form.
Could this feature have been used to gain access to celebrity accounts?
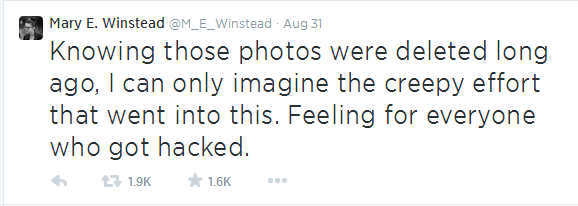 Other celebrities have echoed the sentiment that the photos were taken a long time ago and even deleted.
If that’s the case, then who knows where the hacker got the photos? Maybe he has an inside source at a company which disposes of old celebrity tech hardware (businesses like that exist, right?).
Ultimately, over 100 celebrities including Jennifer Lawrence, Kim Kardashian, Rihanna, Kate Upton, and Selena Gomez were all affected by the leak. iCloud is getting hordes of negative attention in the press.
The hacker isn’t divulging how he gained access to the account. Some have suggested he used a brute force hacking software called iBrute, while others claim he really did find iCloud’s mythical backdoor.
Lesson learned: if you’re storing nude photos on cloud storage, then you should at least encrypt your files.
Or, you know, just use a cloud storage service made by a company that isn’t notorious for its backdoors. In any case, Android may have quietly lost its reputation as the least secure OS – not that the reputation was ever justified.
Other celebrities have echoed the sentiment that the photos were taken a long time ago and even deleted.
If that’s the case, then who knows where the hacker got the photos? Maybe he has an inside source at a company which disposes of old celebrity tech hardware (businesses like that exist, right?).
Ultimately, over 100 celebrities including Jennifer Lawrence, Kim Kardashian, Rihanna, Kate Upton, and Selena Gomez were all affected by the leak. iCloud is getting hordes of negative attention in the press.
The hacker isn’t divulging how he gained access to the account. Some have suggested he used a brute force hacking software called iBrute, while others claim he really did find iCloud’s mythical backdoor.
Lesson learned: if you’re storing nude photos on cloud storage, then you should at least encrypt your files.
Or, you know, just use a cloud storage service made by a company that isn’t notorious for its backdoors. In any case, Android may have quietly lost its reputation as the least secure OS – not that the reputation was ever justified.
 Apple, so far, has remained totally quiet about the leak. People are demanding an explanation.
A truthful response from Apple may look something like this:
“We install secret backdoors on all our devices and operating systems. In this instance, our iCloud backdoor was discovered and infiltrated. We’re not very good at security stuff.”
That’s a truthful response you’ll never get from Apple. Android fans love rubbing Apple’s face into their mistakes. But is Apple really to blame for this leak? Maybe not.
Apple, so far, has remained totally quiet about the leak. People are demanding an explanation.
A truthful response from Apple may look something like this:
“We install secret backdoors on all our devices and operating systems. In this instance, our iCloud backdoor was discovered and infiltrated. We’re not very good at security stuff.”
That’s a truthful response you’ll never get from Apple. Android fans love rubbing Apple’s face into their mistakes. But is Apple really to blame for this leak? Maybe not.
Do all Apple products and services have backdoors?
Apple, like Google and Microsoft, is suspected to have installed backdoors on most of its devices, operating systems, and services. These backdoors are designed to let law enforcement officials or government agencies gain access to private files on various servers. That may have happened here with iCloud. All of the photos appeared to have been stolen from iCloud and metadata from the photos reveals they were taken with iPhones.
If the hacker did gain access to a backdoor, he would theoretically have free access to go around to the iCloud accounts of various celebrities and download all the nude pictures he could find.
That may have happened here with iCloud. All of the photos appeared to have been stolen from iCloud and metadata from the photos reveals they were taken with iPhones.
If the hacker did gain access to a backdoor, he would theoretically have free access to go around to the iCloud accounts of various celebrities and download all the nude pictures he could find.
Or did the hacker simply guess passwords and security questions?
Others claim that the hacker didn’t need to find iCloud’s backdoor. Instead, he simply did the old “forgot my password” trick. In that case, he would have to know the private email addresses/Apple IDs of dozens of celebrities – something that isn’t common knowledge. After clicking the “Forgot my password” link the perpetrator would still have to guess a security question. Unfortunately for celebrities, it’s difficult to setup a secure security question. You can easily find out Jennifer Lawrence’s mom’s maiden name, for example, or read a gossip article talking about where she lived as a kid or what kind of dog she had growing up.
iCloud also has a feature where you don’t need to know the Apple ID at all – you can actually find the Apple ID simply by typing your name, email address, and prior email addresses into a form.
Could this feature have been used to gain access to celebrity accounts?
After clicking the “Forgot my password” link the perpetrator would still have to guess a security question. Unfortunately for celebrities, it’s difficult to setup a secure security question. You can easily find out Jennifer Lawrence’s mom’s maiden name, for example, or read a gossip article talking about where she lived as a kid or what kind of dog she had growing up.
iCloud also has a feature where you don’t need to know the Apple ID at all – you can actually find the Apple ID simply by typing your name, email address, and prior email addresses into a form.
Could this feature have been used to gain access to celebrity accounts?
The photos were “deleted a long time ago”
At least one celebrity has responded to the leak with the following tweet: Other celebrities have echoed the sentiment that the photos were taken a long time ago and even deleted.
If that’s the case, then who knows where the hacker got the photos? Maybe he has an inside source at a company which disposes of old celebrity tech hardware (businesses like that exist, right?).
Ultimately, over 100 celebrities including Jennifer Lawrence, Kim Kardashian, Rihanna, Kate Upton, and Selena Gomez were all affected by the leak. iCloud is getting hordes of negative attention in the press.
The hacker isn’t divulging how he gained access to the account. Some have suggested he used a brute force hacking software called iBrute, while others claim he really did find iCloud’s mythical backdoor.
Lesson learned: if you’re storing nude photos on cloud storage, then you should at least encrypt your files.
Or, you know, just use a cloud storage service made by a company that isn’t notorious for its backdoors. In any case, Android may have quietly lost its reputation as the least secure OS – not that the reputation was ever justified.
Other celebrities have echoed the sentiment that the photos were taken a long time ago and even deleted.
If that’s the case, then who knows where the hacker got the photos? Maybe he has an inside source at a company which disposes of old celebrity tech hardware (businesses like that exist, right?).
Ultimately, over 100 celebrities including Jennifer Lawrence, Kim Kardashian, Rihanna, Kate Upton, and Selena Gomez were all affected by the leak. iCloud is getting hordes of negative attention in the press.
The hacker isn’t divulging how he gained access to the account. Some have suggested he used a brute force hacking software called iBrute, while others claim he really did find iCloud’s mythical backdoor.
Lesson learned: if you’re storing nude photos on cloud storage, then you should at least encrypt your files.
Or, you know, just use a cloud storage service made by a company that isn’t notorious for its backdoors. In any case, Android may have quietly lost its reputation as the least secure OS – not that the reputation was ever justified.
One Click Root Author
One Click Root Author
Content Writer
Experienced writer covering technology and mobile development.
You Might Also Like

iPhone
Android 14 Root Methods: What Changed?
Explore the new root methods and security changes in Android 14.

iPhone
Latest Android Security Updates Impact Root Access
Understanding how the latest security patches affect root methods.
iPhone
Google Pixel 8 Pro Root Guide Released
Complete step-by-step guide to rooting the Google Pixel 8 Pro.
Comments
JD
John Doe
2 days ago
Great article! Very informative and well-written. Thanks for sharing.
JS
Jane Smith
5 days ago
I found the security section particularly helpful. Looking forward to more content like this!
Leave a Comment
Newsletter
Get the latest tech news delivered to your inbox weekly.
Popular Posts
-
1
Getting Started with Android Development
12.5K views
-
2
Best Practices for Mobile Security
8.2K views
-
3
Understanding Smartphone Hardware
6.8K views
