
New TowelRoot Exploit is “Security Nightmare” on Android
3 min read
Last week, TowelRoot shocked the Android community. TowelRoot was created by white hat hacker George Hotz, also known as Geohot, and claims to root any Android device in existence.
The Android world was amazed at TowelRoot – no other rooting method had come anywhere close to working on all devices.
Better yet, running TowelRoot is as easy as installing an app (TowelRoot itself is an APK file). While Android users are enjoying the exploit, the rest of the world is frightened by its security implications.
You see, TowelRoot works on all Android devices because it exploits a section of Android that is found on virtually all Android devices.
That “section” is found in the Linux kernel of Android. While kernels change from device to device, the specifically targeted section is found on almost all Android devices – and even a few desktop Linux kernels.
That exploit wasn’t actually found by Geohot. Instead, it was exposed by an anonymous teenage coder named Pinkie Pie. Mr. Pie encouraged the Linux community to fix the exploit as soon as possible – which is what happened on many desktop Linux kernels.
On Android, fixing that exploit isn’t as easy. All Android code changes need to be passed through manufacturers and carriers – a time-consuming process which will leave Android users exposed for the next few months.
While Android users are enjoying the exploit, the rest of the world is frightened by its security implications.
You see, TowelRoot works on all Android devices because it exploits a section of Android that is found on virtually all Android devices.
That “section” is found in the Linux kernel of Android. While kernels change from device to device, the specifically targeted section is found on almost all Android devices – and even a few desktop Linux kernels.
That exploit wasn’t actually found by Geohot. Instead, it was exposed by an anonymous teenage coder named Pinkie Pie. Mr. Pie encouraged the Linux community to fix the exploit as soon as possible – which is what happened on many desktop Linux kernels.
On Android, fixing that exploit isn’t as easy. All Android code changes need to be passed through manufacturers and carriers – a time-consuming process which will leave Android users exposed for the next few months.
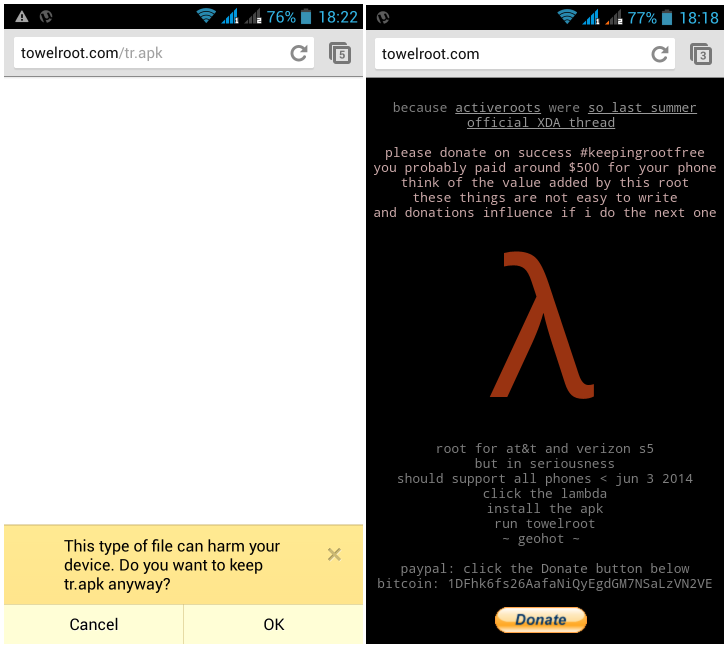 Why is this such a scary thing for the Android community? It’s scary because any app can use this exploit to grant itself root permission without your explicit knowledge.
Installing TowelRoot is as easy as installing a new app. TowelRoot is made by a well-known ethical hacker who fights for the common interest of the people.
But what if a black hat hacker created an app that exploited the same kernel as TowelRoot? What happens if that person then uploads their app to the Google Play Store? Or releases the APK for free online?
If so, all it would take is one click to give a malicious third party root access permissions on your device.
It’s also scary because of how long it takes Android users to receive updates. The Linux kernel exploit can be easily patched, but that update will have to go through the manufacturers and carriers first. How long will that take?
We like to think of rooting as some benevolent activity – and it mostly is. But we are hacking into the Android’s core code by exploiting vulnerabilities. In the right hands, those vulnerabilities help us root. In the wrong hands, they could help a malicious third-party track you, install malware, and ruin your device.
With great power comes great responsibility. Be careful when downloading apps and APK files online from now on. The next app you download could grant itself root access without your explicit permission.
Why is this such a scary thing for the Android community? It’s scary because any app can use this exploit to grant itself root permission without your explicit knowledge.
Installing TowelRoot is as easy as installing a new app. TowelRoot is made by a well-known ethical hacker who fights for the common interest of the people.
But what if a black hat hacker created an app that exploited the same kernel as TowelRoot? What happens if that person then uploads their app to the Google Play Store? Or releases the APK for free online?
If so, all it would take is one click to give a malicious third party root access permissions on your device.
It’s also scary because of how long it takes Android users to receive updates. The Linux kernel exploit can be easily patched, but that update will have to go through the manufacturers and carriers first. How long will that take?
We like to think of rooting as some benevolent activity – and it mostly is. But we are hacking into the Android’s core code by exploiting vulnerabilities. In the right hands, those vulnerabilities help us root. In the wrong hands, they could help a malicious third-party track you, install malware, and ruin your device.
With great power comes great responsibility. Be careful when downloading apps and APK files online from now on. The next app you download could grant itself root access without your explicit permission.
 While Android users are enjoying the exploit, the rest of the world is frightened by its security implications.
You see, TowelRoot works on all Android devices because it exploits a section of Android that is found on virtually all Android devices.
That “section” is found in the Linux kernel of Android. While kernels change from device to device, the specifically targeted section is found on almost all Android devices – and even a few desktop Linux kernels.
That exploit wasn’t actually found by Geohot. Instead, it was exposed by an anonymous teenage coder named Pinkie Pie. Mr. Pie encouraged the Linux community to fix the exploit as soon as possible – which is what happened on many desktop Linux kernels.
On Android, fixing that exploit isn’t as easy. All Android code changes need to be passed through manufacturers and carriers – a time-consuming process which will leave Android users exposed for the next few months.
While Android users are enjoying the exploit, the rest of the world is frightened by its security implications.
You see, TowelRoot works on all Android devices because it exploits a section of Android that is found on virtually all Android devices.
That “section” is found in the Linux kernel of Android. While kernels change from device to device, the specifically targeted section is found on almost all Android devices – and even a few desktop Linux kernels.
That exploit wasn’t actually found by Geohot. Instead, it was exposed by an anonymous teenage coder named Pinkie Pie. Mr. Pie encouraged the Linux community to fix the exploit as soon as possible – which is what happened on many desktop Linux kernels.
On Android, fixing that exploit isn’t as easy. All Android code changes need to be passed through manufacturers and carriers – a time-consuming process which will leave Android users exposed for the next few months.
Why it’s a security threat
 Why is this such a scary thing for the Android community? It’s scary because any app can use this exploit to grant itself root permission without your explicit knowledge.
Installing TowelRoot is as easy as installing a new app. TowelRoot is made by a well-known ethical hacker who fights for the common interest of the people.
But what if a black hat hacker created an app that exploited the same kernel as TowelRoot? What happens if that person then uploads their app to the Google Play Store? Or releases the APK for free online?
If so, all it would take is one click to give a malicious third party root access permissions on your device.
It’s also scary because of how long it takes Android users to receive updates. The Linux kernel exploit can be easily patched, but that update will have to go through the manufacturers and carriers first. How long will that take?
We like to think of rooting as some benevolent activity – and it mostly is. But we are hacking into the Android’s core code by exploiting vulnerabilities. In the right hands, those vulnerabilities help us root. In the wrong hands, they could help a malicious third-party track you, install malware, and ruin your device.
With great power comes great responsibility. Be careful when downloading apps and APK files online from now on. The next app you download could grant itself root access without your explicit permission.
Why is this such a scary thing for the Android community? It’s scary because any app can use this exploit to grant itself root permission without your explicit knowledge.
Installing TowelRoot is as easy as installing a new app. TowelRoot is made by a well-known ethical hacker who fights for the common interest of the people.
But what if a black hat hacker created an app that exploited the same kernel as TowelRoot? What happens if that person then uploads their app to the Google Play Store? Or releases the APK for free online?
If so, all it would take is one click to give a malicious third party root access permissions on your device.
It’s also scary because of how long it takes Android users to receive updates. The Linux kernel exploit can be easily patched, but that update will have to go through the manufacturers and carriers first. How long will that take?
We like to think of rooting as some benevolent activity – and it mostly is. But we are hacking into the Android’s core code by exploiting vulnerabilities. In the right hands, those vulnerabilities help us root. In the wrong hands, they could help a malicious third-party track you, install malware, and ruin your device.
With great power comes great responsibility. Be careful when downloading apps and APK files online from now on. The next app you download could grant itself root access without your explicit permission.
One Click Root Author
One Click Root Author
Content Writer
Experienced writer covering technology and mobile development.
You Might Also Like

Root Android
Android 14 Root Methods: What Changed?
Explore the new root methods and security changes in Android 14.

Root Android
Latest Android Security Updates Impact Root Access
Understanding how the latest security patches affect root methods.
Root Android
Google Pixel 8 Pro Root Guide Released
Complete step-by-step guide to rooting the Google Pixel 8 Pro.
Comments
JD
John Doe
2 days ago
Great article! Very informative and well-written. Thanks for sharing.
JS
Jane Smith
5 days ago
I found the security section particularly helpful. Looking forward to more content like this!
Leave a Comment
Newsletter
Get the latest tech news delivered to your inbox weekly.
Popular Posts
-
1
Getting Started with Android Development
12.5K views
-
2
Best Practices for Mobile Security
8.2K views
-
3
Understanding Smartphone Hardware
6.8K views
